Abstract:
Flex based multimedia system helps us to motivate the students to learn effectively and efficiently.
It helps us to create various audio, vedio tutorials, on various topics using 2D,3D animations which helps the students too learn in better way.
To provide interactive learning techniques.
Facilities approved users to retrieve related information.
To motivate students learn in better way.
To reduce paper work.
To improve the quality of the system.
To satisfy the users.
SCOPE
The supplementary specifications apply to the Flex Based Multimedia system, which is developed in Rational Rose. This specification defines the non-functional requirements of the system such as Reliability, Usability, Availability, Performance and Supportability of security as well as functional requirements that are common across the number of Use Cases.
Flex base multimedia system can be implemented in various Educational institutions to provide effective training to the students.
APPLICATION, OBJECTIVE AND BENEFITS
• APPLICATION
Students located at remote areas will be able to access the tutorials and can enhance their skills at their own time.
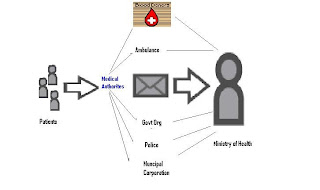 • OBJECTIVES
• OBJECTIVES
To facilitate student community to enhance their skills.
• BENEFITS
Without expensive infrastructure excellent teaching material prepared by trained faculty members can be shared with the student community.
UML
USECASE DIAGRAM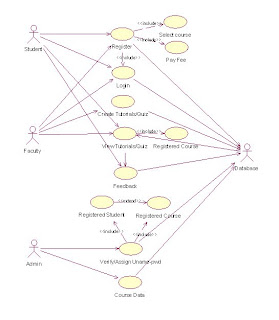 A use case is a set of scenarios that describes an interatction between a user and a system. A use case diagram displays the relationship among actors and use cases. The two main components of a use case diagram are use cases and actors.
A use case is a set of scenarios that describes an interatction between a user and a system. A use case diagram displays the relationship among actors and use cases. The two main components of a use case diagram are use cases and actors.
CLASS DIAGRAM
A class diagram is a type of static structure diagram that describes the structure of a system by showing the system’s classes, their attributes and the relationships between the classes.
SOFTWARE REQUIREMENT SPECIFICATION (SRS)
Overview
a) In the subsequent paragraphs Overall Description, Product Perspective, User Interfaces, Software, Hardware, Communication Protocol, Site Adaptive Requirements and Functional Requirements will be covered.
The glossary contains the working definitions for the key concepts in the Flex Based Multimedia System.
1. Student: A person studying in any educational institution can learn through the various video, audio tutorials and digital stories.
2. Flex: Fast Lexical Analyzer. Flex is collection of technologies released by Adobe Systems for development and deployment of cross platform, rich Internet applications based on the proprietary Adobe Flash Platform.
3. Multimedia: Multimedia is more than one concurrent presentation medium. Multimedia is typically used to mean the combination of text, sound, and/or motion video. Multimedia tends to imply sophistication in both production and presentation than simple text-and-images.
4.Flash: Flash is another technology that allows animations, interactive forms, games and other jazzed-up features to be embedded in web pages. Macromedia Flash player is well known and trustworthy plug-in that users feel comfortable installing.
5. Audio Tutorial: It is the representation of various topics related to various subjects using sound or audio effects.
6. Video Tutorial: It is a representation of various topics using visual effects, which help the students to learn topics in a better way.
7. Digital Stories: Digital Stories, best describes its emphasis on personal voice and facilitative teaching methods. Digital media helps us to craft, rocord, share, and value the stories.
Overall Description:
Flex based Multimedia system helps us to develop products which are very useful for various Educational Organizations. Various diagrams represent what the actual processing goes on in the Project.
Product Functions
Database Functions
1. Database should have the facility to
a) insert records,
b) update,
c) edit,
d) delete (Restricted users only),
e) Search and
f) sort records.
g) Create and edit master and transaction records.
h) All the interaction to and from the database should be through Web Pages.
i) Database should have following tables:-
I. Data Entry Personnel: First Name, Last Name, Address, Contact Details, Qualification, Place of work, Designation. etc
II. Data Entry Points: Ex Hospital, Name of the Hospital, Contact Details, Address etc
III. Disease Details Name, History, Threshold value etc
IV. Health Ministry: Name Details, Designation, contact details etc
V. XML Generate XML database.
Authentication Users at all levels should be authenticated before giving them access.
Analysis Outputs of all analysis should be in the form of
a) Data in tabular form
b) Graphical representation of analysis
c) Threshold values to be indicated.
4. Email General guidelines should be as under:-
a) To box. (mandatory) provide validations.
b) From box (mandatory) provide validation
c) CC box provide validations.
d) BCC box provide validations.
e) Subject box (mandatory)
f) content box (short message of not more than 300 characters) (mandatory)
g) There is no provision for attachments
User Characteristics
Following are the characteristics of the intended users:-
Educational Level. Level of the users is between Educated to highly educated.
Experience Experienced in their domain but need training in the proposed application.
Technical Expertise Training required in the proposed application
Constraints
Following will limit the design and implementation options:-
(a) Only authorized users can access the application
(b) Rights will be given only when payments are made
(c) User need to install Flex software
(d) User need to use SQL server
(e) Hardware limitations: Following HW will be used:-
I. Pentium 4 processor,
II. RAM Minimum 1 GB memory,
III. 40 GB Hard disk.
(f) Interface to other applications: Interaction between ASP.NET 2.0 and Flex takes place using Web Services. Connectivity from ASP.NET 2.0 to SQL Server is done using ADO.NET.
(g) Parallel operation: Auto backup of database after every one hour.
(h) Audit functions: Authentication of users, emails, patient details and NW security.
(i) Control functions
I. Access policy: set who (user, process) is authorized to access to what (resource like server, directory, process, user...) and how (for running, reading...), and who is not authorized to access to what.
II. exchange XML documents through FTP links
(j) Higher-order language requirements
(k) Reliability requirements
I. Stronger user loyalty
II. Lowhere risk
(l) Criticality of the application Analysis and sending of email to health ministry are safety-critical modules. Failure of these modules could cause catastrophic consequences for human life.
• High-level (Test cases for threshold values)requirements are developed
• Low-level requirements comply with high-level requirements
• Source code complies with low-level requirements
• Source code is traceable to low-level requirements
(m) Safety and security considerations Some of the characteristics of the safety critical operation are the performing of
I. Database integrity checking with each read and write into a database,
II. Range checking,
III. Continuous checking of the hardware and problem logging.
IV. Eliminate data redundancy
V. Database information validation
VI. Hardware validation and
VII. Variable data validation including range testing and format testing.
Assumptions and Dependencies
It is assumed that all the systems will have the basic HW, SW and Communication Interfaces available. The users are trained in using the application.
Apportioning of Requirements
Identify requirements that may be delayed until future versions of the system.
All requirements will be met.
Performance Requirements
Presently we are working on four terminals. It is expected that at any point of time three terminals will be in operation simultaneously. The amount of information will be numerical and text oriented and the volume will be limited.
Logical Database Requirements
Logical requirements connected with the database include:
a) Most of the values are string types but the count is in numbers.
b) Accessing rights are limited to authenticated users only.
c) Integrity constraints are maintained by setting the relationships.
d) Data will be retained as per the policy of the Education Ministry requirements
Design Constraints
Hardware Constraints
IV. Pentium 4 processor,
V. RAM Minimum 1 GB memory,
VI. 40 GB Hard disk.
VII. 100 Mbps Modem
Design constraints
(n) Charts have to be created using Flex
(o) All user interfaces have to be created using Flex
(p) Interaction between User Interface and the database should be through Web Services.
Standards Compliance
Following standards will be maintained:-
a) Report format (Email to Education Ministry as per format)
b) Data naming (As per the Naming Conventions – organization policy)
c) Accounting procedures
d) Audit Tracing (All changes made to student details will be traced in trace files with before and after values)
Software System Attributes
Analysis: Identifying authorized students and make the tutorial avaible to them only for the duration of the course:
Modular approach
1. Check for authenticated users
2. Make only those tutorials available to the students for which they have registered
3. Quiz results should be shown to the students
4. Students should be able to rate the tutorials
Reliability
Software will be handed over to the client after carrwet extensive
• Unit Testing
• Integration Testing
• System Testing
• After performing periodic demonstrations to the end users on completion of each module and keep a log of the errors / observations made by the user
• Number of errors during Unit Testing may be more but they should show decreasing trend during Integration and System Testing and should reduce to zero at the time of delivery.
Ensure strict compliance to Project Plan
Availability
Specify the factors required to guarantee a defined availability level for the entire system such as checkpoint, recovery, and restart.
Security
Authentication module will ensure that only authorized users are provided access control on the web site.
Roles will be defined to impose restrictions on the authorized users.
Ensure that buffer overflow and integer overflow will be avoided.
Whenever user is deleted his privileges will also get deleted.
Carrwet periodic backup of the database and maintain a log.
Honey Pots Intentionally include some PCs in the network which are vulnerable for hackers. They can be used to catch hackers or fix vulnerability.
Maintainability
Keep a count of the number of lines of code. Though there cannot be a benchmark for the maximum lines of code in a sub routine but higher the lines of code indicates
• Higher is the maintenance.
• Need to split up in to child levels.
• Place every module in TryCatch() and Finally() block to prevent disgraceful exit.
Avoid excessive complexity
Avoid excessive Inheritance
Variable name should not match the field names
Reduce complexity of conditional branching
1.13 Portability
Specify attributes of software that relate to the ease of porting the software to other host machines and/or operating systems. This may include
a) Percentage of components with host-dependent code
b) Percentage of code that is host dependent
c) Use of a proven portable language
d) Use of a particular compiler or language subset
System Mode
Some systems behave quite differently depending on the mode of operation. For example, a control system may have different sets of functions depending on its mode: training, normal, or emergency. When organizing by mode there are two possible outlines. The choice depends on whether interfaces and performance are dependent on mode.
Web Site being developed in ASP.NET 2.0 it is compatible to most of the OS and the Web Browsers.
User Class
Students
Faculty members.
Administrator
Objects
Following objects are being considered in this application:-
• Authorized users.
• Students
• Faculty members
• Tutorials
• Quiz
Use Cases
Feature
The features are listed in the subsequent paragraphs in the form of Stimulus and Response.
Stimulus
User ID + Pwd of Authorized Users
Selection of Quiz
String event for searching tutorial
Response to review by students
Response
Author Alert
Questions for quiz
Display of tutorials as per search parameter
Updating of rating table
Functional Hierarchy
When none of the above organizational schemes prove helpful, the overall functionality can be organized into a hierarchy of functions organized by common inputs, common outputs, or common internal data access. Data flow diagrams and data dictionaries can be used to show the relationships between and among the functions and data.
Draw DFDs
Prepare Data Dictionaries.
Supporting Information
The supporting information makes the SRS easier to use. It includes:
(a) Table of Contents at the front of the document
(b) Index
(c) Appendices: Definitions of important terminologies are given in the Appendix A.
The Appendices are not always considered part of the actual requirements specification and are not always necessary. They may include:
(a) Sample I/O formats, descriptions of cost analysis studies, results of user surveys;
(b) Supporting or background information that can help the readers of the SRS;
(c) A description of the problems to be solved by the software;
When Appendices are included, the SRS should explicitly state whether or not the Appendices are to be considered part of the requirements.
PHASE MODULE 1
Authentication & Verification.
In this module students will create their account for registering any online courses and once registration process is completed, he will be authenticated to view his activity.
MODULE 2
Accessing the WebPages.
In this module user can access ASP.Net web pages created with the help of flex programming & help in integrating tutorials, presentations, digital stories, etc.
MODULE 3
View data & Information Module.
In this module students can search for the desired tutorials by units, channels & videos. For example, if students request details for 3D Animation in search will have find 3D Animation related topics which they are interested. But the students will have no privileges to download the topic.
If students select videotape the web services is invoked & that particular web services will fetch the data.
CONCLUSION
Scope of project is high.
This project have more scope in future & it can be integrated in other institutions, repository for storing the data in date bases as in central.
FURTHER ENHANCEMENTS
Students can search for the desired tutorials by units, channels & videos.
Students to learn effectively and efficiently.
Students located at remote areas will be able to access the tutorials and can enhance their skills at their own time.
It helps us to create various audio, vedio tutorials, on various topics using 2D,3D animations which helps the students too learn in better way.
To provide interactive learning techniques.
Facilities approved users to retrieve related information.
To motivate students learn in better way.
To reduce paper work.
To improve the quality of the system.
To satisfy the users.
SCOPE
The supplementary specifications apply to the Flex Based Multimedia system, which is developed in Rational Rose. This specification defines the non-functional requirements of the system such as Reliability, Usability, Availability, Performance and Supportability of security as well as functional requirements that are common across the number of Use Cases.
Flex base multimedia system can be implemented in various Educational institutions to provide effective training to the students.
APPLICATION, OBJECTIVE AND BENEFITS
• APPLICATION
Students located at remote areas will be able to access the tutorials and can enhance their skills at their own time.
 • OBJECTIVES
• OBJECTIVESTo facilitate student community to enhance their skills.
• BENEFITS
Without expensive infrastructure excellent teaching material prepared by trained faculty members can be shared with the student community.
UML
USECASE DIAGRAM
 A use case is a set of scenarios that describes an interatction between a user and a system. A use case diagram displays the relationship among actors and use cases. The two main components of a use case diagram are use cases and actors.
A use case is a set of scenarios that describes an interatction between a user and a system. A use case diagram displays the relationship among actors and use cases. The two main components of a use case diagram are use cases and actors.CLASS DIAGRAM
A class diagram is a type of static structure diagram that describes the structure of a system by showing the system’s classes, their attributes and the relationships between the classes.
SOFTWARE REQUIREMENT SPECIFICATION (SRS)
Overview
a) In the subsequent paragraphs Overall Description, Product Perspective, User Interfaces, Software, Hardware, Communication Protocol, Site Adaptive Requirements and Functional Requirements will be covered.
The glossary contains the working definitions for the key concepts in the Flex Based Multimedia System.
1. Student: A person studying in any educational institution can learn through the various video, audio tutorials and digital stories.
2. Flex: Fast Lexical Analyzer. Flex is collection of technologies released by Adobe Systems for development and deployment of cross platform, rich Internet applications based on the proprietary Adobe Flash Platform.
3. Multimedia: Multimedia is more than one concurrent presentation medium. Multimedia is typically used to mean the combination of text, sound, and/or motion video. Multimedia tends to imply sophistication in both production and presentation than simple text-and-images.
4.Flash: Flash is another technology that allows animations, interactive forms, games and other jazzed-up features to be embedded in web pages. Macromedia Flash player is well known and trustworthy plug-in that users feel comfortable installing.
5. Audio Tutorial: It is the representation of various topics related to various subjects using sound or audio effects.
6. Video Tutorial: It is a representation of various topics using visual effects, which help the students to learn topics in a better way.
7. Digital Stories: Digital Stories, best describes its emphasis on personal voice and facilitative teaching methods. Digital media helps us to craft, rocord, share, and value the stories.
Overall Description:
Flex based Multimedia system helps us to develop products which are very useful for various Educational Organizations. Various diagrams represent what the actual processing goes on in the Project.
Product Functions
Database Functions
1. Database should have the facility to
a) insert records,
b) update,
c) edit,
d) delete (Restricted users only),
e) Search and
f) sort records.
g) Create and edit master and transaction records.
h) All the interaction to and from the database should be through Web Pages.
i) Database should have following tables:-
I. Data Entry Personnel: First Name, Last Name, Address, Contact Details, Qualification, Place of work, Designation. etc
II. Data Entry Points: Ex Hospital, Name of the Hospital, Contact Details, Address etc
III. Disease Details Name, History, Threshold value etc
IV. Health Ministry: Name Details, Designation, contact details etc
V. XML Generate XML database.
Authentication Users at all levels should be authenticated before giving them access.
Analysis Outputs of all analysis should be in the form of
a) Data in tabular form
b) Graphical representation of analysis
c) Threshold values to be indicated.
4. Email General guidelines should be as under:-
a) To box. (mandatory) provide validations.
b) From box (mandatory) provide validation
c) CC box provide validations.
d) BCC box provide validations.
e) Subject box (mandatory)
f) content box (short message of not more than 300 characters) (mandatory)
g) There is no provision for attachments
User Characteristics
Following are the characteristics of the intended users:-
Educational Level. Level of the users is between Educated to highly educated.
Experience Experienced in their domain but need training in the proposed application.
Technical Expertise Training required in the proposed application
Constraints
Following will limit the design and implementation options:-
(a) Only authorized users can access the application
(b) Rights will be given only when payments are made
(c) User need to install Flex software
(d) User need to use SQL server
(e) Hardware limitations: Following HW will be used:-
I. Pentium 4 processor,
II. RAM Minimum 1 GB memory,
III. 40 GB Hard disk.
(f) Interface to other applications: Interaction between ASP.NET 2.0 and Flex takes place using Web Services. Connectivity from ASP.NET 2.0 to SQL Server is done using ADO.NET.
(g) Parallel operation: Auto backup of database after every one hour.
(h) Audit functions: Authentication of users, emails, patient details and NW security.
(i) Control functions
I. Access policy: set who (user, process) is authorized to access to what (resource like server, directory, process, user...) and how (for running, reading...), and who is not authorized to access to what.
II. exchange XML documents through FTP links
(j) Higher-order language requirements
(k) Reliability requirements
I. Stronger user loyalty
II. Lowhere risk
(l) Criticality of the application Analysis and sending of email to health ministry are safety-critical modules. Failure of these modules could cause catastrophic consequences for human life.
• High-level (Test cases for threshold values)requirements are developed
• Low-level requirements comply with high-level requirements
• Source code complies with low-level requirements
• Source code is traceable to low-level requirements
(m) Safety and security considerations Some of the characteristics of the safety critical operation are the performing of
I. Database integrity checking with each read and write into a database,
II. Range checking,
III. Continuous checking of the hardware and problem logging.
IV. Eliminate data redundancy
V. Database information validation
VI. Hardware validation and
VII. Variable data validation including range testing and format testing.
Assumptions and Dependencies
It is assumed that all the systems will have the basic HW, SW and Communication Interfaces available. The users are trained in using the application.
Apportioning of Requirements
Identify requirements that may be delayed until future versions of the system.
All requirements will be met.
Performance Requirements
Presently we are working on four terminals. It is expected that at any point of time three terminals will be in operation simultaneously. The amount of information will be numerical and text oriented and the volume will be limited.
Logical Database Requirements
Logical requirements connected with the database include:
a) Most of the values are string types but the count is in numbers.
b) Accessing rights are limited to authenticated users only.
c) Integrity constraints are maintained by setting the relationships.
d) Data will be retained as per the policy of the Education Ministry requirements
Design Constraints
Hardware Constraints
IV. Pentium 4 processor,
V. RAM Minimum 1 GB memory,
VI. 40 GB Hard disk.
VII. 100 Mbps Modem
Design constraints
(n) Charts have to be created using Flex
(o) All user interfaces have to be created using Flex
(p) Interaction between User Interface and the database should be through Web Services.
Standards Compliance
Following standards will be maintained:-
a) Report format (Email to Education Ministry as per format)
b) Data naming (As per the Naming Conventions – organization policy)
c) Accounting procedures
d) Audit Tracing (All changes made to student details will be traced in trace files with before and after values)
Software System Attributes
Analysis: Identifying authorized students and make the tutorial avaible to them only for the duration of the course:
Modular approach
1. Check for authenticated users
2. Make only those tutorials available to the students for which they have registered
3. Quiz results should be shown to the students
4. Students should be able to rate the tutorials
Reliability
Software will be handed over to the client after carrwet extensive
• Unit Testing
• Integration Testing
• System Testing
• After performing periodic demonstrations to the end users on completion of each module and keep a log of the errors / observations made by the user
• Number of errors during Unit Testing may be more but they should show decreasing trend during Integration and System Testing and should reduce to zero at the time of delivery.
Ensure strict compliance to Project Plan
Availability
Specify the factors required to guarantee a defined availability level for the entire system such as checkpoint, recovery, and restart.
Security
Authentication module will ensure that only authorized users are provided access control on the web site.
Roles will be defined to impose restrictions on the authorized users.
Ensure that buffer overflow and integer overflow will be avoided.
Whenever user is deleted his privileges will also get deleted.
Carrwet periodic backup of the database and maintain a log.
Honey Pots Intentionally include some PCs in the network which are vulnerable for hackers. They can be used to catch hackers or fix vulnerability.
Maintainability
Keep a count of the number of lines of code. Though there cannot be a benchmark for the maximum lines of code in a sub routine but higher the lines of code indicates
• Higher is the maintenance.
• Need to split up in to child levels.
• Place every module in TryCatch() and Finally() block to prevent disgraceful exit.
Avoid excessive complexity
Avoid excessive Inheritance
Variable name should not match the field names
Reduce complexity of conditional branching
1.13 Portability
Specify attributes of software that relate to the ease of porting the software to other host machines and/or operating systems. This may include
a) Percentage of components with host-dependent code
b) Percentage of code that is host dependent
c) Use of a proven portable language
d) Use of a particular compiler or language subset
System Mode
Some systems behave quite differently depending on the mode of operation. For example, a control system may have different sets of functions depending on its mode: training, normal, or emergency. When organizing by mode there are two possible outlines. The choice depends on whether interfaces and performance are dependent on mode.
Web Site being developed in ASP.NET 2.0 it is compatible to most of the OS and the Web Browsers.
User Class
Students
Faculty members.
Administrator
Objects
Following objects are being considered in this application:-
• Authorized users.
• Students
• Faculty members
• Tutorials
• Quiz
Use Cases
Feature
The features are listed in the subsequent paragraphs in the form of Stimulus and Response.
Stimulus
User ID + Pwd of Authorized Users
Selection of Quiz
String event for searching tutorial
Response to review by students
Response
Author Alert
Questions for quiz
Display of tutorials as per search parameter
Updating of rating table
Functional Hierarchy
When none of the above organizational schemes prove helpful, the overall functionality can be organized into a hierarchy of functions organized by common inputs, common outputs, or common internal data access. Data flow diagrams and data dictionaries can be used to show the relationships between and among the functions and data.
Draw DFDs
Prepare Data Dictionaries.
Supporting Information
The supporting information makes the SRS easier to use. It includes:
(a) Table of Contents at the front of the document
(b) Index
(c) Appendices: Definitions of important terminologies are given in the Appendix A.
The Appendices are not always considered part of the actual requirements specification and are not always necessary. They may include:
(a) Sample I/O formats, descriptions of cost analysis studies, results of user surveys;
(b) Supporting or background information that can help the readers of the SRS;
(c) A description of the problems to be solved by the software;
When Appendices are included, the SRS should explicitly state whether or not the Appendices are to be considered part of the requirements.
PHASE MODULE 1
Authentication & Verification.
In this module students will create their account for registering any online courses and once registration process is completed, he will be authenticated to view his activity.
MODULE 2
Accessing the WebPages.
In this module user can access ASP.Net web pages created with the help of flex programming & help in integrating tutorials, presentations, digital stories, etc.
MODULE 3
View data & Information Module.
In this module students can search for the desired tutorials by units, channels & videos. For example, if students request details for 3D Animation in search will have find 3D Animation related topics which they are interested. But the students will have no privileges to download the topic.
If students select videotape the web services is invoked & that particular web services will fetch the data.
CONCLUSION
Scope of project is high.
This project have more scope in future & it can be integrated in other institutions, repository for storing the data in date bases as in central.
FURTHER ENHANCEMENTS
Students can search for the desired tutorials by units, channels & videos.
Students to learn effectively and efficiently.
Students located at remote areas will be able to access the tutorials and can enhance their skills at their own time.

Post a Comment